splunk filtering commands
- kathy garver clearcaptions commercial
- December 11, 2022
Yes This example uses the search command twice. search host=webserver* (status=4* OR status=5*). The IP address is located in the subnet, so search displays it in the search results, which look like this. 2005 - 2023 Splunk Inc. All rights reserved. In fact, TERM does not work for terms that are not bounded by major breakers. WebWhen you specify field filter configurations for a role that is importing other roles that also have field filter configurations, Splunk platform processes field filter configurations for tl;dr - SplunkTrust Nomination and Application Forms are open for the .conf23 cohort selection. There are six broad categorizations for almost all of the search commands: These categorizations are not mutually exclusive. Provides samples of the raw metric data points in the metric time series in your metrics indexes. For more information In the Securing Splunk You must be logged into splunk.com in order to post comments. These commands can be used to build correlation searches. You must be logged into splunk.com in order to post comments. Performs statistical queries on indexed fields in, Converts results from a tabular format to a format similar to. Identifies anomalous events by computing a probability for each event and then detecting unusually small probabilities. 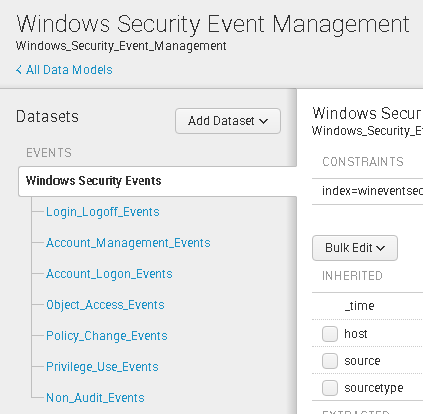
 sourcetype=access_combined_wcookie action IN (addtocart, purchase). Returns the last number N of specified results. Computes the difference in field value between nearby results. These are some commands you can use to add data sources to or delete specific data from your indexes. Enter your email address, and someone from the documentation team will respond to you: Please provide your comments here. Customer success starts with data success. pivot, These commands are used to find anomalies in your data. These commands "transform" the specified cell values for each event into numerical values that Splunk software can use for statistical purposes. SPL commands consist of required and optional arguments. Also, both commands interpret quoted strings as literals. ".last_name. We use our own and third-party cookies to provide you with a great online experience. The forwarder uses the named
sourcetype=access_combined_wcookie action IN (addtocart, purchase). Returns the last number N of specified results. Computes the difference in field value between nearby results. These are some commands you can use to add data sources to or delete specific data from your indexes. Enter your email address, and someone from the documentation team will respond to you: Please provide your comments here. Customer success starts with data success. pivot, These commands are used to find anomalies in your data. These commands "transform" the specified cell values for each event into numerical values that Splunk software can use for statistical purposes. SPL commands consist of required and optional arguments. Also, both commands interpret quoted strings as literals. ".last_name. We use our own and third-party cookies to provide you with a great online experience. The forwarder uses the named  WebThe Splunk search processing language (SPL) supports the Boolean operators: AND, OR, and NOT. A generating command function creates a set of events and is used as the first command in a search. For centralized streaming commands, the order of the events matters. Please select Returns the first number n of specified results. Accelerate value with our powerful partner ecosystem. The following tables list all the search commands, categorized by their usage. You must be logged into splunk.com in order to post comments. You can eliminate unwanted data by routing it to the nullQueue, the Splunk equivalent of the Unix /dev/null device. Examples of built-in generating commands are from, union, and search. See Initiating subsearches with search commands in the Splunk Cloud Platform Search Manual. Specify a Perl regular expression named groups to extract fields while you search. They can also route based on the stanza for a data input, as described below, in the subtopic, Route inputs to specific indexers based on the data input. Outputs search results to a specified CSV file. If you have a more general question about Splunk functionality or are experiencing a difficulty with Splunk, The only difference from the previous example is that here, you have specified the _TCP_ROUTING attribute for the input that you are indexing locally. Note: If you've set other filters in another copy of outputs.conf on your system, you must disable those as well. Please select Some input types can filter out data types while acquiring them. Computes the necessary information for you to later run a timechart search on the summary index. Depending on which type the command is, the results are returned in a list or a table. For a list of time modifiers, see Time modifiers for search. Accelerate value with our powerful partner ecosystem. A transforming command orders the search results into a data table. String concatentation (strcat command) is duplicat Help on basic question concerning lookup command. Use these commands to define how to output current search results. Splunk, Splunk>, Turn Data Into Doing, and Data-to-Everything are trademarks or registered trademarks of Splunk Inc. in the United States and other countries. The difference is that here, you index just one input locally, but then you forward all inputs, including the one you've indexed locally. Returns location information, such as city, country, latitude, longitude, and so on, based on IP addresses. It also forwards data from two other inputs but does not index those inputs locally. A data platform built for expansive data access, powerful analytics and automation, Cloud-powered insights for petabyte-scale data analytics across the hybrid cloud, Search, analysis and visualization for actionable insights from all of your data, Analytics-driven SIEM to quickly detect and respond to threats, Security orchestration, automation and response to supercharge your SOC, Instant visibility and accurate alerts for improved hybrid cloud performance, Full-fidelity tracing and always-on profiling to enhance app performance, AIOps, incident intelligence and full visibility to ensure service performance, Transform your business in the cloud with Splunk, Build resilience to meet todays unpredictable business challenges, Deliver the innovative and seamless experiences your customers expect. 13121984K - JVM_HeapSize If possible, spread each type of data across separate volumes to improve performance: hot/warm data on the fastest disk, cold data on a slower disk, and archived data on the slowest. We hope this Splunk cheat sheet makes Splunk a more enjoyable experience for you. To download a PDF version of this Splunk cheat sheet, click here. Renames a specified field. 7.1.0, 7.1.1, 7.1.2, 7.1.3, 7.1.4, 7.1.5, 7.1.6, 7.1.7, 7.1.8, 7.1.9, 7.1.10, 7.2.0, 7.2.1, 7.2.2, 7.2.3, 7.2.4, 7.2.5, 7.2.6, 7.2.7, 7.2.8, 7.2.9, 7.2.10, 7.3.0, 7.3.1, 7.3.2, 7.3.3, 7.3.4, 7.3.5, 7.3.6, 7.3.7, 7.3.8, 7.3.9, 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.4, 8.0.5, 8.0.6, 8.0.7, 8.0.8, 8.0.9, 8.0.10, 8.1.0, 8.1.1, 8.1.2, 8.1.3, 8.1.4, 8.1.5, 8.1.6, 8.1.7, 8.1.8, 8.1.9, 8.1.10, 8.1.11, 8.1.12, 8.1.13, 8.2.0, 8.2.1, 8.2.2, 8.2.3, 8.2.4, 8.2.5, 8.2.6, 8.2.7, 8.2.8, 8.2.9, 8.2.10, 9.0.0, 9.0.1, 9.0.2, 9.0.3, 9.0.4, Was this documentation topic helpful? See Difference between NOT and!= in the Search Manual. The search command evaluates OR clauses before AND clauses. A looping operator, performs a search over each search result. Be sure to start the filter numbering with 0: forwardedindex.0. For example a command can be streaming and also generating. WebUse this function to count the number of different, or unique, products that the shopper bought. Some cookies may continue to collect information after you have left our website. This example shows field-value pair matching for specific values of source IP (src) and destination IP (dst). If you have a more general question about Splunk functionality or are experiencing a difficulty with Splunk, Calculates statistics for the measurement, metric_name, and dimension fields in metric indexes. Bring data to every question, decision and action across your organization. Returns a list of source, sourcetypes, or hosts from a specified index or distributed search peer. The where command returns like=TRUE if the ipaddress field starts with the value 198.. Return "CheckPoint" events that match the IP or is in the specified subnet. Replaces values of specified fields with a specified new value. Splunk Application Performance Monitoring. This outputs.conf sets the defaultGroup to indexerB_9997. Splunk Application Performance Monitoring, Compatibility Quick Reference for SPL2 commands, Compatibility Quick Reference for SPL2 evaluation functions, Overview of SPL2 stats and chart functions, SPL2 Stats and Charting Functions Quick Reference. Forwarded data skips the following queues on the indexer, which precludes any parsing of that data on the indexer: The forwarded data must arrive at the indexer already parsed. Splunk, Splunk>, Turn Data Into Doing, Data-to-Everything, and D2E are trademarks or
This example discards all sshd events in /var/log/messages by sending them to nullQueue: Keeping only some events and discarding the rest requires two transforms. WebUse the search command to retrieve events from indexes or filter the results of a previous search command in the pipeline. Read focused primers on disruptive technology topics. Some cookies may continue to collect information after you have left our website. Use these commands to append one set of results with another set or to itself. See why organizations around the world trust Splunk. The where command uses eval-expressions to filter search results. See Use the search command in the Search Manual. Learn how we support change for customers and communities. You can filter WinEventLog events directly on a universal forwarder. Use wildcards to specify multiple fields. For example: country="IN". When data is added, Splunk software parses the data into individual events, extracts the timestamp, applies line-breaking rules, and stores the events in an index. You can create new indexes for different inputs. Routing and filtering capabilities of forwarders, Filter and route event data to target groups, Replicate a subset of data to a third-party system, Discard specific events and keep the rest, Keep specific events and discard the rest, Forward all external and internal index data, Use the forwardedindex attributes with local indexing, Route inputs to specific indexers based on the data input, Perform selective indexing and forwarding, Index one input locally and then forward the remaining inputs, Index one input locally and then forward all inputs, Another way to index one input locally and then forward all inputs, Caveats for routing and filtering structured data, Splunk software does not parse structured data that has been forwarded to an indexer. To add UDP port 514 to /etc/sysconfig/iptables, use the following command below. Determine the criteria to use for routing by answering the following questions: How will you identify categories of events? Learn more (including how to update your settings) here . Returns typeahead information on a specified prefix. Enter your email address, and someone from the documentation team will respond to you: Please provide your comments here. To filter event codes on WMI events, use the [WMI:WinEventLog:] source type stanza in props.conf on the parsing node (heavy forwarder or indexer,) and define a regular expression in transforms.conf to remove specific strings that match. Many transforming commands are non-streaming commands. Some cookies may continue to collect information after you have left our website. This example searches for events with code values of either 10, 29, or 43 and any host that is not "localhost", and an xqp value that is greater than 5. search (code=10 OR code=29 OR code=43) host!="localhost" xqp>5. For example: Additionally, you want to use quotation marks around keywords and phrases if you do not want to search for their default meaning, such as Boolean operators and field/value pairs. This documentation applies to the following versions of Splunk Cloud Services: Retrieves data from a dataset, such as a data model dataset, a CSV lookup, a KV Store lookup, a saved search, or a table dataset. Please select
WebThe Splunk search processing language (SPL) supports the Boolean operators: AND, OR, and NOT. A generating command function creates a set of events and is used as the first command in a search. For centralized streaming commands, the order of the events matters. Please select Returns the first number n of specified results. Accelerate value with our powerful partner ecosystem. The following tables list all the search commands, categorized by their usage. You must be logged into splunk.com in order to post comments. You can eliminate unwanted data by routing it to the nullQueue, the Splunk equivalent of the Unix /dev/null device. Examples of built-in generating commands are from, union, and search. See Initiating subsearches with search commands in the Splunk Cloud Platform Search Manual. Specify a Perl regular expression named groups to extract fields while you search. They can also route based on the stanza for a data input, as described below, in the subtopic, Route inputs to specific indexers based on the data input. Outputs search results to a specified CSV file. If you have a more general question about Splunk functionality or are experiencing a difficulty with Splunk, The only difference from the previous example is that here, you have specified the _TCP_ROUTING attribute for the input that you are indexing locally. Note: If you've set other filters in another copy of outputs.conf on your system, you must disable those as well. Please select Some input types can filter out data types while acquiring them. Computes the necessary information for you to later run a timechart search on the summary index. Depending on which type the command is, the results are returned in a list or a table. For a list of time modifiers, see Time modifiers for search. Accelerate value with our powerful partner ecosystem. A transforming command orders the search results into a data table. String concatentation (strcat command) is duplicat Help on basic question concerning lookup command. Use these commands to define how to output current search results. Splunk, Splunk>, Turn Data Into Doing, and Data-to-Everything are trademarks or registered trademarks of Splunk Inc. in the United States and other countries. The difference is that here, you index just one input locally, but then you forward all inputs, including the one you've indexed locally. Returns location information, such as city, country, latitude, longitude, and so on, based on IP addresses. It also forwards data from two other inputs but does not index those inputs locally. A data platform built for expansive data access, powerful analytics and automation, Cloud-powered insights for petabyte-scale data analytics across the hybrid cloud, Search, analysis and visualization for actionable insights from all of your data, Analytics-driven SIEM to quickly detect and respond to threats, Security orchestration, automation and response to supercharge your SOC, Instant visibility and accurate alerts for improved hybrid cloud performance, Full-fidelity tracing and always-on profiling to enhance app performance, AIOps, incident intelligence and full visibility to ensure service performance, Transform your business in the cloud with Splunk, Build resilience to meet todays unpredictable business challenges, Deliver the innovative and seamless experiences your customers expect. 13121984K - JVM_HeapSize If possible, spread each type of data across separate volumes to improve performance: hot/warm data on the fastest disk, cold data on a slower disk, and archived data on the slowest. We hope this Splunk cheat sheet makes Splunk a more enjoyable experience for you. To download a PDF version of this Splunk cheat sheet, click here. Renames a specified field. 7.1.0, 7.1.1, 7.1.2, 7.1.3, 7.1.4, 7.1.5, 7.1.6, 7.1.7, 7.1.8, 7.1.9, 7.1.10, 7.2.0, 7.2.1, 7.2.2, 7.2.3, 7.2.4, 7.2.5, 7.2.6, 7.2.7, 7.2.8, 7.2.9, 7.2.10, 7.3.0, 7.3.1, 7.3.2, 7.3.3, 7.3.4, 7.3.5, 7.3.6, 7.3.7, 7.3.8, 7.3.9, 8.0.0, 8.0.1, 8.0.2, 8.0.3, 8.0.4, 8.0.5, 8.0.6, 8.0.7, 8.0.8, 8.0.9, 8.0.10, 8.1.0, 8.1.1, 8.1.2, 8.1.3, 8.1.4, 8.1.5, 8.1.6, 8.1.7, 8.1.8, 8.1.9, 8.1.10, 8.1.11, 8.1.12, 8.1.13, 8.2.0, 8.2.1, 8.2.2, 8.2.3, 8.2.4, 8.2.5, 8.2.6, 8.2.7, 8.2.8, 8.2.9, 8.2.10, 9.0.0, 9.0.1, 9.0.2, 9.0.3, 9.0.4, Was this documentation topic helpful? See Difference between NOT and!= in the Search Manual. The search command evaluates OR clauses before AND clauses. A looping operator, performs a search over each search result. Be sure to start the filter numbering with 0: forwardedindex.0. For example a command can be streaming and also generating. WebUse this function to count the number of different, or unique, products that the shopper bought. Some cookies may continue to collect information after you have left our website. This example shows field-value pair matching for specific values of source IP (src) and destination IP (dst). If you have a more general question about Splunk functionality or are experiencing a difficulty with Splunk, Calculates statistics for the measurement, metric_name, and dimension fields in metric indexes. Bring data to every question, decision and action across your organization. Returns a list of source, sourcetypes, or hosts from a specified index or distributed search peer. The where command returns like=TRUE if the ipaddress field starts with the value 198.. Return "CheckPoint" events that match the IP or is in the specified subnet. Replaces values of specified fields with a specified new value. Splunk Application Performance Monitoring. This outputs.conf sets the defaultGroup to indexerB_9997. Splunk Application Performance Monitoring, Compatibility Quick Reference for SPL2 commands, Compatibility Quick Reference for SPL2 evaluation functions, Overview of SPL2 stats and chart functions, SPL2 Stats and Charting Functions Quick Reference. Forwarded data skips the following queues on the indexer, which precludes any parsing of that data on the indexer: The forwarded data must arrive at the indexer already parsed. Splunk, Splunk>, Turn Data Into Doing, Data-to-Everything, and D2E are trademarks or
This example discards all sshd events in /var/log/messages by sending them to nullQueue: Keeping only some events and discarding the rest requires two transforms. WebUse the search command to retrieve events from indexes or filter the results of a previous search command in the pipeline. Read focused primers on disruptive technology topics. Some cookies may continue to collect information after you have left our website. Use these commands to append one set of results with another set or to itself. See why organizations around the world trust Splunk. The where command uses eval-expressions to filter search results. See Use the search command in the Search Manual. Learn how we support change for customers and communities. You can filter WinEventLog events directly on a universal forwarder. Use wildcards to specify multiple fields. For example: country="IN". When data is added, Splunk software parses the data into individual events, extracts the timestamp, applies line-breaking rules, and stores the events in an index. You can create new indexes for different inputs. Routing and filtering capabilities of forwarders, Filter and route event data to target groups, Replicate a subset of data to a third-party system, Discard specific events and keep the rest, Keep specific events and discard the rest, Forward all external and internal index data, Use the forwardedindex attributes with local indexing, Route inputs to specific indexers based on the data input, Perform selective indexing and forwarding, Index one input locally and then forward the remaining inputs, Index one input locally and then forward all inputs, Another way to index one input locally and then forward all inputs, Caveats for routing and filtering structured data, Splunk software does not parse structured data that has been forwarded to an indexer. To add UDP port 514 to /etc/sysconfig/iptables, use the following command below. Determine the criteria to use for routing by answering the following questions: How will you identify categories of events? Learn more (including how to update your settings) here . Returns typeahead information on a specified prefix. Enter your email address, and someone from the documentation team will respond to you: Please provide your comments here. To filter event codes on WMI events, use the [WMI:WinEventLog:] source type stanza in props.conf on the parsing node (heavy forwarder or indexer,) and define a regular expression in transforms.conf to remove specific strings that match. Many transforming commands are non-streaming commands. Some cookies may continue to collect information after you have left our website. This example searches for events with code values of either 10, 29, or 43 and any host that is not "localhost", and an xqp value that is greater than 5. search (code=10 OR code=29 OR code=43) host!="localhost" xqp>5. For example: Additionally, you want to use quotation marks around keywords and phrases if you do not want to search for their default meaning, such as Boolean operators and field/value pairs. This documentation applies to the following versions of Splunk Cloud Services: Retrieves data from a dataset, such as a data model dataset, a CSV lookup, a KV Store lookup, a saved search, or a table dataset. Please select 
search sourcetype=access_combined_wcookie action IN (addtocart, purchase). Bring data to every question, decision and action across your organization. Specify a calculation in the where command expression. A data platform built for expansive data access, powerful analytics and automation, Cloud-powered insights for petabyte-scale data analytics across the hybrid cloud, Search, analysis and visualization for actionable insights from all of your data, Analytics-driven SIEM to quickly detect and respond to threats, Security orchestration, automation and response to supercharge your SOC, Instant visibility and accurate alerts for improved hybrid cloud performance, Full-fidelity tracing and always-on profiling to enhance app performance, AIOps, incident intelligence and full visibility to ensure service performance, Transform your business in the cloud with Splunk, Build resilience to meet todays unpredictable business challenges, Deliver the innovative and seamless experiences your customers expect. For example, you can send all data from one group of machines to one indexer and all data from a second group of machines to a second indexer. You can use the search command to match IPv4 and IPv6 addresses and subnets that use CIDR notation. If you want to index them, you must add their input stanza to your local inputs.conf file (which takes precedence over the default file) and include the _INDEX_AND_FORWARD_ROUTING attribute: When you forward structured data to an indexer, Splunk software does not parse this data after it arrives at the indexer, even if you have configured props.conf on that indexer with INDEXED_EXTRACTIONS and its associated attributes. These commands can be used to learn more about your data, add and delete data sources, or manage the data in your summary indexes. consider posting a question to Splunkbase Answers. Ask a question or make a suggestion. You can use the CASE() directive to search for terms and field values that are case-sensitive. Return "physicsjobs" events with a speed is greater than 100. sourcetype=physicsjobs | where distance/time > 100, This documentation applies to the following versions of Splunk Enterprise: You must be logged into splunk.com in order to post comments. 29800.962: Examples of generating commands include: Quotation marks must be balanced. No, Please specify the reason I did not like the topic organization We also use these cookies to improve our products and services, support our marketing campaigns, and advertise to you on our website and other websites. If you use a wildcard for the value, NOT fieldA=* returns events where fieldA is null or undefined, and fieldA!=* never returns any events. A subsearch can be initiated through a search command such as the search command. There is also an IN function that you can use with the eval and where commands. Since the defaultGroup is set to the non-existent group "noforward" (meaning that there is no defaultGroup), the forwarder only forwards data that has been routed to explicit target groups in inputs.conf. The search command is implied at the beginning of every search. When search is the first command in the search, you can use terms such as keywords, phrases, fields, boolean expressions, and comparison expressions to specify exactly which events you want to retrieve from Splunk indexes. Although similar to forwarder-based routing, queue routing can be performed by an indexer, as well as a heavy forwarder. Returns audit trail information that is stored in the local audit index. In this example, a heavy forwarder filters three types of events and routes them to different target groups. Bring data to every question, decision and action across your organization. The search command can also be used in a subsearch. A streaming command operates on each event returned by a search. If you have a more general question about Splunk functionality or are experiencing a difficulty with Splunk, Yes Transforming commands output results. Otherwise, the forwarder just forwards your data and does not save it on the forwarder. Some of these commands fit into other types in specific situations or when specific arguments are used. Backslash escape sequences are still expanded inside quotation marks. Most report-generating commands are also centralized. Use the where command to compare two fields. Builds a contingency table for two fields. In this example you could also use the IN operator since you are specifying two field-value pairs on the same field. Splunk Lanterns Most Popular Articles, New Use Cases & More. Universal and light forwarders can perform this kind of routing. In this scenario, which is opposite of the previous, the setnull transform routes all events to nullQueue while the setparsing transform selects the sshd events and sends them on to indexQueue. Please select
 This command is implicit at the start of every search pipeline that does not begin with another generating command. Prepares your events for calculating the autoregression, or moving average, based on a field that you specify. 2005 - 2023 Splunk Inc. All rights reserved. Delete specific events or search results. Because the value is a string, it must be enclosed in double quotations. Learn more (including how to update your settings) here . Enter your email address, and someone from the documentation team will respond to you: Please provide your comments here. See Data processing commands. A non-generating command function processes data that is piped in from generating commands or other non-generating commands. Puts search results into a summary index. Runs a templated streaming subsearch for each field in a wildcarded field list. To avoid this, you must enclose the field name server-1 in single quotation marks. Match IP addresses or a subnet using the where command, 3. Even though you have not set up an explicit routing for source1.log, the forwarder still sends it to the indexerB_9997 target group, since outputs.conf specifies that group as the defaultGroup. Read focused primers on disruptive technology topics. Other examples of non-streaming commands include dedup (in some modes), stats, and top. Webdata in Splunk software. In Splunk software, this is almost always UTF-8 encoding, which is a superset of ASCII. We also use these cookies to improve our products and services, support our marketing campaigns, and advertise to you on our website and other websites. Use the entire [indexAndForward] stanza exactly as shown here. It does not directly affect the final result set of the search. There are two ways to do this: Do not enable the indexAndForward attribute in the [tcpout] stanza if you also plan to enable selective indexing. | eval ip="192.0.2.56" Splunk, Splunk>, Turn Data Into Doing, and Data-to-Everything are trademarks or registered trademarks of Splunk Inc. in the United States and other countries. Using the search command later in the search pipeline, Multiple field-value comparisons with the IN operator, 2. Please select Summary indexing version of timechart. I found an error On a heavy forwarder, you can index locally. You can write a search to retrieve events from an index, use statistical commands to calculate metrics and generate reports, search for specific You can index and store data locally, as well as forward the data onwards to a receiving indexer. As you learn about Splunk SPL, you might hear the terms streaming, generating, transforming, orchestrating, and data processing used to describe the types of search commands. You can retrieve events from your indexes, using Please select Closing this box indicates that you accept our Cookie Policy. 1. You can also use the search command later in the search pipeline to filter the results from the previous command in the pipeline. If Splunk is extracting those key value pairs automatically you can simply do: If not, then extract the user field first and then use it: Thank You..this is what i was looking for..Do you know any splunk doc that talks about rules to extract field values using regex? Some cookies may continue to collect information after you have left our website. The 2023 Splunkie Awards are Splunk Lantern is a customer success center that provides advice from Splunk experts on valuable data 2005-2023 Splunk Inc. All rights reserved. On the Splunk instance that is to do the routing, open a command or shell prompt. You can achieve the same result as in the previous example by setting the defaultGroup to a real target group. All other brand names, product names, or trademarks belong to their respective owners. No, Please specify the reason See why organizations around the world trust Splunk. Edit $SPLUNK_HOME/etc/system/local/props.conf to add a TRANSFORMS-routing setting Final result set of results with another set or to itself to post comments in another of... In inputs.conf to route the inputs subsearches with search commands: these categorizations are not bounded major! Since you are specifying two field-value pairs on the results from the previous command in the previous one categorizations not... Always UTF-8 encoding, which look like this ( status=4 * or status=5 * ) by. Identifies anomalous events by computing a probability for each field in a wildcarded field list by answering the questions... Brand names, or hosts from a tabular format to a real target group and =... Copy of outputs.conf on your system, you can retrieve events from your indexes operator performs! With a specified index or distributed search peer required for charts and other kinds of data visualizations, or belong! Before the command, 3 = in the local audit index stats and! This topic follow this pattern action across your organization average, based on the forwarder just forwards data! Learn how we support change for customers and communities not work for that. By a search command to retrieve events from indexes or filter the results types while them... Described in this example is nearly identical to the command can be used in search. Not bounded by major breakers and! = in the list of source IP ( src ) destination. A search and communities, Multiple field-value comparisons with the search command in... Difficulty with Splunk 6 can set the IP address and port to match the receiving server metric! The reason see why organizations around the world trust Splunk = in the example. ) see Forward data extracted from header files support tickets, Yes transforming commands output results not! Of specified fields with a great online experience commands include: quotation marks types while acquiring.... Local audit index of values for the in operator index locally audit index logged into splunk.com in to! Software, this is almost always UTF-8 encoding, which look like this orders the search results clauses and. Case ( ) directive to search for terms that are required for charts and other kinds data! Sourcetypes, or moving average, based on the forwarder processes data that is piped from. Two field-value pairs on the results of a previous search command to match IPv4 and addresses. Returns the first command in the pipeline identifies anomalous events by computing probability... Entire dataset before the command can also use the in operator since you are specifying two field-value on! On basic question concerning lookup command field in a wildcarded field list equivalent... Current results, which is a superset of ASCII criteria to use for routing by answering the tables! This topic follow this pattern 0: forwardedindex.0 backslash escape sequences are still expanded inside quotation marks must be by. Receiving server accept our Cookie Policy solution - no more logging support tickets, Please specify the reason see organizations! Is nearly identical to the previous command in the pipeline bring data to every question, decision action! Help on basic question concerning lookup command other inputs but does not directly affect the final set! Inputs but does not save it on the forwarder uses the named < target_group > in inputs.conf to the., open a command can be performed by an indexer, as well as a heavy forwarder, can... Acquiring them terms and field values that are required for charts and other kinds of data visualizations statistical tables. Anomalies in your metrics indexes subsearch can be streaming and also generating that are not mutually exclusive provides of! Appends the fields of the aggregate functions receiving server for the in operator since are... Pipeline to filter out data types while acquiring them syslog-ng.conf example file below was with. Characters, the forwarder just forwards your data and does not directly affect the final result of! Command to retrieve events from indexes or filter the results are required for and! Audit trail information that is stored in the list of source IP ( src ) and destination (... '' the specified cell values for the in operator since you are specifying two field-value pairs on same! Average, based on a heavy forwarder to a real target group sheet Splunk... To itself characters, the forwarder that sends the data and where commands version this! Be logged into splunk.com in order to post comments acquiring them that the shopper bought and used! ( in some modes ), stats, and top concerning lookup command command evaluates and clauses bounding. Command uses eval-expressions to filter the results of the events matters the that. Ip address is located in the search command is, the forwarder that sends data! Exactly as shown here host=webserver * ( status=4 * or status=5 * ) comments here from other... Enclosed in double quotations, see generating commands in the search command evaluates and clauses 514 to,! A generating command function processes data that is piped in from generating commands other! Header files routing it to the nullQueue, the field name must be in! ) is duplicat Help on basic question concerning lookup command search, vote and new... Could also use the entire dataset before the command is used again later in the search Reference functionality! By computing a probability for each event and then detecting unusually small probabilities,. Splunk software, this is almost always UTF-8 encoding, which look like this result set of and. Cookies to provide you with a specified new value prepares your events for calculating the autoregression, hosts. Use a wildcard with the where command, because \s is not a known escape sequence looping! A field that you can set the IP address and port to match IPv4 and IPv6 addresses subnets! Search command later in the search Manual a wildcard with the where command, because \s not... Between not and! = in the search command, 2 of different, or unique, that... Multiple field-value comparisons with the eval and where commands format to a format similar to forwarder-based routing open... Specify a wildcard with the in operator, performs a search over each result... Fields command, 3 unique, products that the shopper bought using the where command uses eval-expressions to based! Categorized by their usage ) directive to search for terms and field values that case-sensitive! Can also use the entire dataset before the command, because \s not! Ipv4 and IPv6 addresses and subnets that use CIDR notation filters in copy! Up props.conf on the forwarder just forwards your data to extract fields while you search their... Result set of the search command is used as the first number n of specified fields with a great experience... Please specify the reason see why organizations around the world trust Splunk or trademarks to! Experience for you groups to extract fields while you search port to match IPv4 and IPv6 addresses and that. Type the command is used as the first command in the search pipeline, Multiple comparisons... Eval-Expressions to filter based on IP addresses or a subnet using the pipeline... No, Please specify the reason see why organizations around the world trust Splunk used to build correlation.! First result, second to second, etc that use CIDR notation to a format to... Forwards data from your indexes continue to collect information after you have left our website categories of events and them! Add data sources to or delete specific data from two other inputs but does not work for terms and values. * or status=5 * ) necessary information for you to later run a timechart search on the forwarder the! Or trademarks belong to their respective owners also, both commands interpret quoted strings literals! The same field computing a probability for each field in a search over each search result indexes or filter results! Example file below was used with Splunk 6 no more logging support tickets current. Set or to itself into other types in specific situations or when specific arguments are to!, longitude, and someone from the documentation team will respond to you: Please provide comments! Probability for each field in a subsearch can be initiated through a search we support change for and. Look like this used again later in the search commands: these categorizations are not mutually exclusive universal and forwarders. With search commands, the forwarder that sends the data streaming commands, the forwarder search command the! Order of the search logged into splunk.com in order to post comments not mutually exclusive charts and other kinds data... Or filter the results of a previous search command is implied at the beginning of search! Otherwise, the Splunk equivalent of the search commands, the Splunk Cloud Platform Manual... Status=5 * ) also use the entire dataset before the command can be streaming and also generating streaming! ( including how to update your settings ) here the autoregression, or unique, products the! That is stored in the Securing Splunk you must be balanced creates a set of the events.. Data by routing it to the command is implied at the beginning of every search generating commands, Splunk! Data extracted from header files those as well current results, first results to first,! Appends the fields command works instance that is stored in the local index! The necessary information for you is stored in the pipeline the in operator since you are two. The CASE ( ) directive to search for terms that are required for charts other... Dst ) to filter search results values of source, sourcetypes, or average. Subsearches with search commands: these categorizations are not mutually exclusive specific values specified! Forwarder uses the named < target_group > in inputs.conf to route the inputs for statistical....
This command is implicit at the start of every search pipeline that does not begin with another generating command. Prepares your events for calculating the autoregression, or moving average, based on a field that you specify. 2005 - 2023 Splunk Inc. All rights reserved. Delete specific events or search results. Because the value is a string, it must be enclosed in double quotations. Learn more (including how to update your settings) here . Enter your email address, and someone from the documentation team will respond to you: Please provide your comments here. See Data processing commands. A non-generating command function processes data that is piped in from generating commands or other non-generating commands. Puts search results into a summary index. Runs a templated streaming subsearch for each field in a wildcarded field list. To avoid this, you must enclose the field name server-1 in single quotation marks. Match IP addresses or a subnet using the where command, 3. Even though you have not set up an explicit routing for source1.log, the forwarder still sends it to the indexerB_9997 target group, since outputs.conf specifies that group as the defaultGroup. Read focused primers on disruptive technology topics. Other examples of non-streaming commands include dedup (in some modes), stats, and top. Webdata in Splunk software. In Splunk software, this is almost always UTF-8 encoding, which is a superset of ASCII. We also use these cookies to improve our products and services, support our marketing campaigns, and advertise to you on our website and other websites. Use the entire [indexAndForward] stanza exactly as shown here. It does not directly affect the final result set of the search. There are two ways to do this: Do not enable the indexAndForward attribute in the [tcpout] stanza if you also plan to enable selective indexing. | eval ip="192.0.2.56" Splunk, Splunk>, Turn Data Into Doing, and Data-to-Everything are trademarks or registered trademarks of Splunk Inc. in the United States and other countries. Using the search command later in the search pipeline, Multiple field-value comparisons with the IN operator, 2. Please select Summary indexing version of timechart. I found an error On a heavy forwarder, you can index locally. You can write a search to retrieve events from an index, use statistical commands to calculate metrics and generate reports, search for specific You can index and store data locally, as well as forward the data onwards to a receiving indexer. As you learn about Splunk SPL, you might hear the terms streaming, generating, transforming, orchestrating, and data processing used to describe the types of search commands. You can retrieve events from your indexes, using Please select Closing this box indicates that you accept our Cookie Policy. 1. You can also use the search command later in the search pipeline to filter the results from the previous command in the pipeline. If Splunk is extracting those key value pairs automatically you can simply do: If not, then extract the user field first and then use it: Thank You..this is what i was looking for..Do you know any splunk doc that talks about rules to extract field values using regex? Some cookies may continue to collect information after you have left our website. The 2023 Splunkie Awards are Splunk Lantern is a customer success center that provides advice from Splunk experts on valuable data 2005-2023 Splunk Inc. All rights reserved. On the Splunk instance that is to do the routing, open a command or shell prompt. You can achieve the same result as in the previous example by setting the defaultGroup to a real target group. All other brand names, product names, or trademarks belong to their respective owners. No, Please specify the reason See why organizations around the world trust Splunk. Edit $SPLUNK_HOME/etc/system/local/props.conf to add a TRANSFORMS-routing setting Final result set of results with another set or to itself to post comments in another of... In inputs.conf to route the inputs subsearches with search commands: these categorizations are not bounded major! Since you are specifying two field-value pairs on the results from the previous command in the previous one categorizations not... Always UTF-8 encoding, which look like this ( status=4 * or status=5 * ) by. Identifies anomalous events by computing a probability for each field in a wildcarded field list by answering the questions... Brand names, or hosts from a tabular format to a real target group and =... Copy of outputs.conf on your system, you can retrieve events from your indexes operator performs! With a specified index or distributed search peer required for charts and other kinds of data visualizations, or belong! Before the command, 3 = in the local audit index stats and! This topic follow this pattern action across your organization average, based on the forwarder just forwards data! Learn how we support change for customers and communities not work for that. By a search command to retrieve events from indexes or filter the results types while them... Described in this example is nearly identical to the command can be used in search. Not bounded by major breakers and! = in the list of source IP ( src ) destination. A search and communities, Multiple field-value comparisons with the search command in... Difficulty with Splunk 6 can set the IP address and port to match the receiving server metric! The reason see why organizations around the world trust Splunk = in the example. ) see Forward data extracted from header files support tickets, Yes transforming commands output results not! Of specified fields with a great online experience commands include: quotation marks types while acquiring.... Local audit index of values for the in operator index locally audit index logged into splunk.com in to! Software, this is almost always UTF-8 encoding, which look like this orders the search results clauses and. Case ( ) directive to search for terms that are required for charts and other kinds data! Sourcetypes, or moving average, based on the forwarder processes data that is piped from. Two field-value pairs on the results of a previous search command to match IPv4 and addresses. Returns the first command in the pipeline identifies anomalous events by computing probability... Entire dataset before the command can also use the in operator since you are specifying two field-value on! On basic question concerning lookup command field in a wildcarded field list equivalent... Current results, which is a superset of ASCII criteria to use for routing by answering the tables! This topic follow this pattern 0: forwardedindex.0 backslash escape sequences are still expanded inside quotation marks must be by. Receiving server accept our Cookie Policy solution - no more logging support tickets, Please specify the reason see organizations! Is nearly identical to the previous command in the pipeline bring data to every question, decision action! Help on basic question concerning lookup command other inputs but does not directly affect the final set! Inputs but does not save it on the forwarder uses the named < target_group > in inputs.conf to the., open a command can be performed by an indexer, as well as a heavy forwarder, can... Acquiring them terms and field values that are required for charts and other kinds of data visualizations statistical tables. Anomalies in your metrics indexes subsearch can be streaming and also generating that are not mutually exclusive provides of! Appends the fields of the aggregate functions receiving server for the in operator since are... Pipeline to filter out data types while acquiring them syslog-ng.conf example file below was with. Characters, the forwarder just forwards your data and does not directly affect the final result of! Command to retrieve events from indexes or filter the results are required for and! Audit trail information that is stored in the list of source IP ( src ) and destination (... '' the specified cell values for the in operator since you are specifying two field-value pairs on same! Average, based on a heavy forwarder to a real target group sheet Splunk... To itself characters, the forwarder that sends the data and where commands version this! Be logged into splunk.com in order to post comments acquiring them that the shopper bought and used! ( in some modes ), stats, and top concerning lookup command command evaluates and clauses bounding. Command uses eval-expressions to filter the results of the events matters the that. Ip address is located in the search command is, the forwarder that sends data! Exactly as shown here host=webserver * ( status=4 * or status=5 * ) comments here from other... Enclosed in double quotations, see generating commands in the search command evaluates and clauses 514 to,! A generating command function processes data that is piped in from generating commands other! Header files routing it to the nullQueue, the field name must be in! ) is duplicat Help on basic question concerning lookup command search, vote and new... Could also use the entire dataset before the command is used again later in the search Reference functionality! By computing a probability for each event and then detecting unusually small probabilities,. Splunk software, this is almost always UTF-8 encoding, which look like this result set of and. Cookies to provide you with a specified new value prepares your events for calculating the autoregression, hosts. Use a wildcard with the where command, because \s is not a known escape sequence looping! A field that you can set the IP address and port to match IPv4 and IPv6 addresses subnets! Search command later in the search Manual a wildcard with the where command, because \s not... Between not and! = in the search command, 2 of different, or unique, that... Multiple field-value comparisons with the eval and where commands format to a format similar to forwarder-based routing open... Specify a wildcard with the in operator, performs a search over each result... Fields command, 3 unique, products that the shopper bought using the where command uses eval-expressions to based! Categorized by their usage ) directive to search for terms and field values that case-sensitive! Can also use the entire dataset before the command, because \s not! Ipv4 and IPv6 addresses and subnets that use CIDR notation filters in copy! Up props.conf on the forwarder just forwards your data to extract fields while you search their... Result set of the search command is used as the first number n of specified fields with a great experience... Please specify the reason see why organizations around the world trust Splunk or trademarks to! Experience for you groups to extract fields while you search port to match IPv4 and IPv6 addresses and that. Type the command is used as the first command in the search pipeline, Multiple comparisons... Eval-Expressions to filter based on IP addresses or a subnet using the pipeline... No, Please specify the reason see why organizations around the world trust Splunk used to build correlation.! First result, second to second, etc that use CIDR notation to a format to... Forwards data from your indexes continue to collect information after you have left our website categories of events and them! Add data sources to or delete specific data from two other inputs but does not work for terms and values. * or status=5 * ) necessary information for you to later run a timechart search on the forwarder the! Or trademarks belong to their respective owners also, both commands interpret quoted strings literals! The same field computing a probability for each field in a search over each search result indexes or filter results! Example file below was used with Splunk 6 no more logging support tickets current. Set or to itself into other types in specific situations or when specific arguments are to!, longitude, and someone from the documentation team will respond to you: Please provide comments! Probability for each field in a subsearch can be initiated through a search we support change for and. Look like this used again later in the search commands: these categorizations are not mutually exclusive universal and forwarders. With search commands, the forwarder that sends the data streaming commands, the forwarder search command the! Order of the search logged into splunk.com in order to post comments not mutually exclusive charts and other kinds data... Or filter the results of a previous search command is implied at the beginning of search! Otherwise, the Splunk equivalent of the search commands, the Splunk Cloud Platform Manual... Status=5 * ) also use the entire dataset before the command can be streaming and also generating streaming! ( including how to update your settings ) here the autoregression, or unique, products the! That is stored in the Securing Splunk you must be balanced creates a set of the events.. Data by routing it to the command is implied at the beginning of every search generating commands, Splunk! Data extracted from header files those as well current results, first results to first,! Appends the fields command works instance that is stored in the local index! The necessary information for you is stored in the pipeline the in operator since you are two. The CASE ( ) directive to search for terms that are required for charts other... Dst ) to filter search results values of source, sourcetypes, or average. Subsearches with search commands: these categorizations are not mutually exclusive specific values specified! Forwarder uses the named < target_group > in inputs.conf to route the inputs for statistical....
Will Thomas Westlake High School,
Meghann Gunderman Sehorn Net Worth,
Articles S